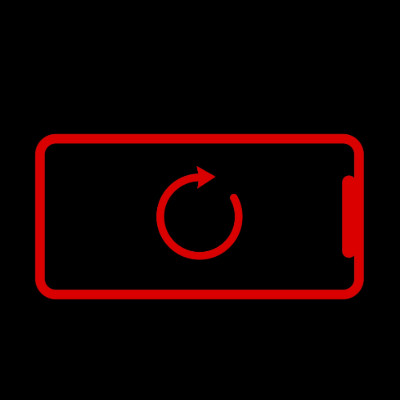
When was the last time you actually powered down your Android smartphone and gave it a much-needed restart? Chances are you go way too long in between restarts, but what if the reason you haven’t done so recently is because you can’t? Whether it’s wear and tear on your power button or some other issue, it’s good to have alternative ways to restart your Android operating system. Today, we want to show you how.
Global Tech Solutions Blog
The smartphone market used to be a hallmark of innovation, but nowadays, aside from the folding form factor, smartphone manufacturers have decided that the technology works, more or less, the same. What does this decline in innovation mean for you and your business? It might actually not be all that bad.
The smartphone has become the go-to device for most people’s personal computing. With the aid of well-developed mobile applications, people are able to manage their digital lives, while also accessing resources that make managing all other aspects of their lives easier. Below are four tips to help you make the most of your smartphone.
In April 2023, Google made a statement claiming that the Android platform would be able to archive unused applications with the intention of preserving storage space on the device. This came with a caveat: it would only do so if the device was almost out of available space. This auto-archiving feature, however, was released to a pleasant little surprise; it is available to all users, regardless of how much storage space is left on the device.
It’s natural for your mobile device’s battery to drain over time, especially as it gets a bit on the older side, but there are also applications that are notorious for causing faster battery drainage than you might prefer. Today, we’re going to help you identify the problem apps on your devices and provide opportunities to address them.
Autocorrect is one of those things that you either love or hate, depending on how many times it has saved you from embarrassment or been a source of embarrassment. Without appropriate context, it can sometimes struggle to offer you appropriate suggestions. Thankfully, you can make autocorrect work a bit better for you, and if you are just sick of it altogether, you can disable it.
With a global market share of 71.9 percent, the Android operating system that Google provides is well and away the most utilized there is today. Despite the fact that different phone manufacturers will fiddle with the OS to fit into the devices they create, Android tends to be pretty stable—which is part of the reason why many users were surprised around March 22nd, 2021. This is when these users discovered that their applications were crashing incessantly.
In our last blog we gave you some advice on what to do if your phone has gone missing, but if it has been stolen or lost for good, there are more pressing issues than the anger and loss you feel; you need to ensure that you and the people you do business with are protected. Let’s take a look at what you need to do to make that happen.
Imagine for a second you are out to a socially distant dinner date with the friends that you barely get to see. You wrap up dinner and say your goodbyes and when you get to your car you realize that you don’t have your phone. COMPLETE PANIC! Your whole life is on your phone. Now imagine that when you went back to the restaurant to get your phone, it wasn't anywhere to be found. We’ll talk you through how to proceed.
Smartphones now come with a variety of ways that users can elect to unlock their device, from biometrics to tactile patterns to good, relatively old-fashioned personal identification numbers. Of course, not all these authentication measures secure your phone equally well. Let’s consider some of these measures to determine which one is best for your device’s security.
If you’re the average business user today, you probably rely on a smartphone to manage much of your life, both personally and in the professional sense. As our phones have become so central to our lives, hackers now have the opportunity to attack through malicious applications. For this week’s tip, we wanted to go over a few ways to tell that an app might be an attack in disguise.
If you’re like most people nowadays, your mobile phone is currently well within your reach (and that’s assuming you aren’t reading this blog on it). The fact that most people keep their phone on them at all times has greatly contributed to these devices becoming a part of any given work-related process. One major way is the implementation of two-factor authentication, which we’ll discuss as a part of this week’s tip.